Introduction
PHP is a popular server-side scripting language widely used for web development. While it offers flexibility and ease of use, developers often make mistakes that can impact the security, performance, and maintainability of their code. In this article, we’ll explore the top 10 mistakes that PHP developers should avoid to build robust and efficient applications.
- Ignoring Security Best Practices:
Security should be a top priority in web development. Failing to validate user inputs, using outdated encryption methods, and neglecting to secure sensitive data can lead to serious vulnerabilities. PHP developers should always follow best practices for input validation, use parameterized queries to prevent SQL injection, and stay informed about the latest security threats. - Not Using Prepared Statements:
One common mistake is not using prepared statements when working with databases. Prepared statements help prevent SQL injection attacks by separating SQL code from user input, making it more secure and efficient. - Poor Error Handling:
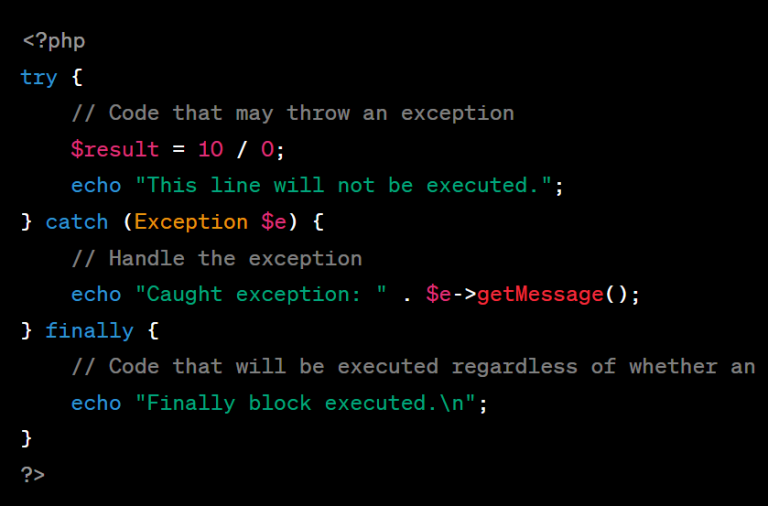
Inadequate error handling can make debugging and maintenance challenging. Developers should implement proper error reporting and logging mechanisms to catch and handle errors gracefully. Displaying detailed error messages on a production site is a security risk and should be avoided. - Ignoring Code Readability and Maintainability:
Writing code that is difficult to read and understand can hinder collaboration and future maintenance. PHP developers should adhere to coding standards, use meaningful variable and function names, and apply consistent indentation to enhance code readability. - Overlooking Code Documentation:
Proper documentation is essential for understanding and maintaining code. Neglecting to document functions, classes, and overall code structure can result in confusion for both the developer and anyone who works with the code in the future. - Excessive Use of Global Variables:
Overusing global variables can lead to unpredictable behavior and make debugging challenging. PHP developers should limit the use of global variables and prefer passing data through function parameters or using class properties. - Not Optimizing Database Queries:
Inefficient database queries can significantly impact application performance. Developers should optimize their SQL queries, use proper indexing, and consider caching mechanisms to reduce the load on the database. - Ignoring PHP Version Compatibility:
PHP evolves over time, introducing new features and deprecating old ones. Ignoring version compatibility can lead to issues when migrating or deploying applications. Developers should stay updated on the PHP version their code is running on and adapt accordingly. - Not Using Composer for Dependency Management:
Composer is a powerful tool for managing PHP dependencies, yet some developers still neglect its use. Not leveraging Composer can result in manual dependency management headaches, version conflicts, and difficulties in maintaining third-party libraries. - Skipping Regular Code Reviews:
Code reviews are crucial for identifying and fixing issues early in the development process. Skipping regular code reviews can lead to the accumulation of technical debt, making it harder to address problems later. PHP developers should prioritize collaborative code reviews to ensure code quality.
By avoiding these common mistakes, PHP developers can create more secure, maintainable, and efficient applications. It’s essential to stay informed about best practices, continuously improve coding skills, and embrace a mindset of continuous learning to deliver high-quality PHP projects.
Sample Code
Certainly! Let’s provide examples for a few of the mentioned mistakes to illustrate better. Note that the following code snippets intentionally contain mistakes for demonstration purposes.
1. Ignoring Security Best Practices:
// Incorrect: Not validating user input $userInput = $_GET['username']; // Vulnerable to SQL injection $query = "SELECT * FROM users WHERE username = '$userInput'";
Corrected Version:
// Correct: Using parameterized queries for input validation
$userInput = $_GET['username'];
$stmt = $pdo->prepare("SELECT * FROM users WHERE username = :username");
$stmt->bindParam(':username', $userInput);
$stmt->execute();2. Not Using Prepared Statements:
// Incorrect: Directly embedding user input into SQL query
$userInput = $_POST['user_input'];
$query = "INSERT INTO users (name) VALUES ('$userInput')";Corrected Version:
// Correct: Using prepared statements to prevent SQL injection
$userInput = $_POST['user_input'];
$stmt = $pdo->prepare("INSERT INTO users (name) VALUES (?)");
$stmt->execute([$userInput]);3. Poor Error Handling:
// Incorrect: Displaying detailed error messages on a production site
ini_set('display_errors', 1);
error_reporting(E_ALL);
// ... rest of the code ...Corrected Version:
// Correct: Logging errors instead of displaying on production
ini_set('display_errors', 0);
error_reporting(0);
// Log errors to a file
ini_set('log_errors', 1);
ini_set('error_log', '/path/to/error.log');
// ... rest of the code ...These examples highlight just a few of the mentioned mistakes and their corrected versions. Remember that secure and maintainable code often involves a combination of good practices rather than individual fixes. Always adapt these practices based on your specific use case and requirements.