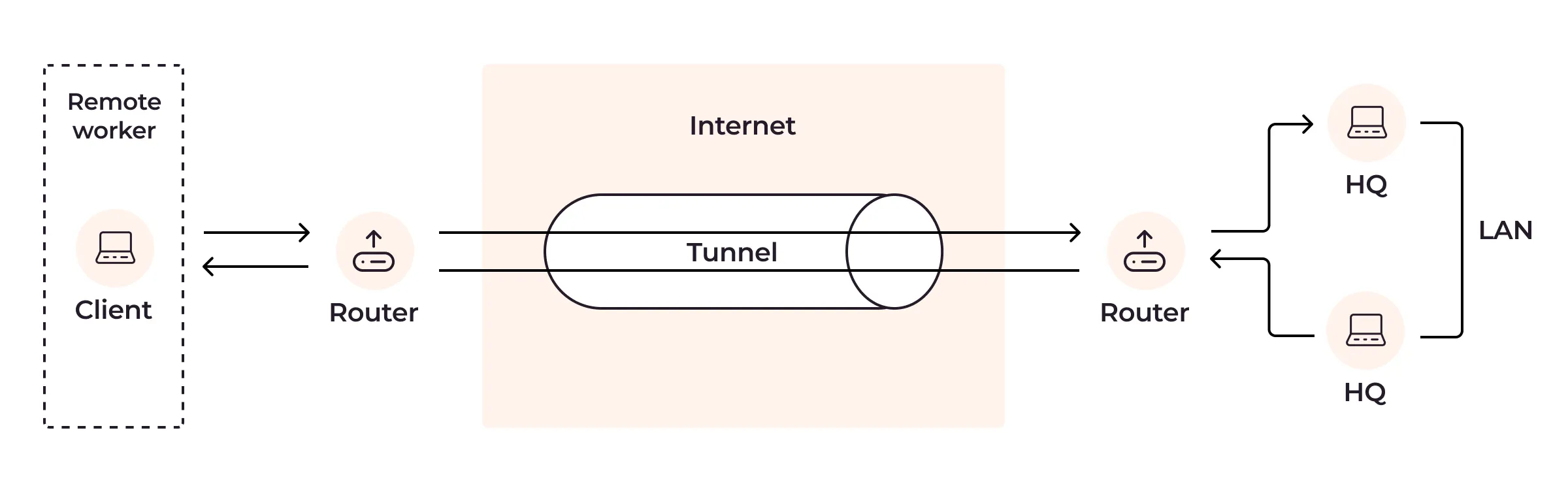
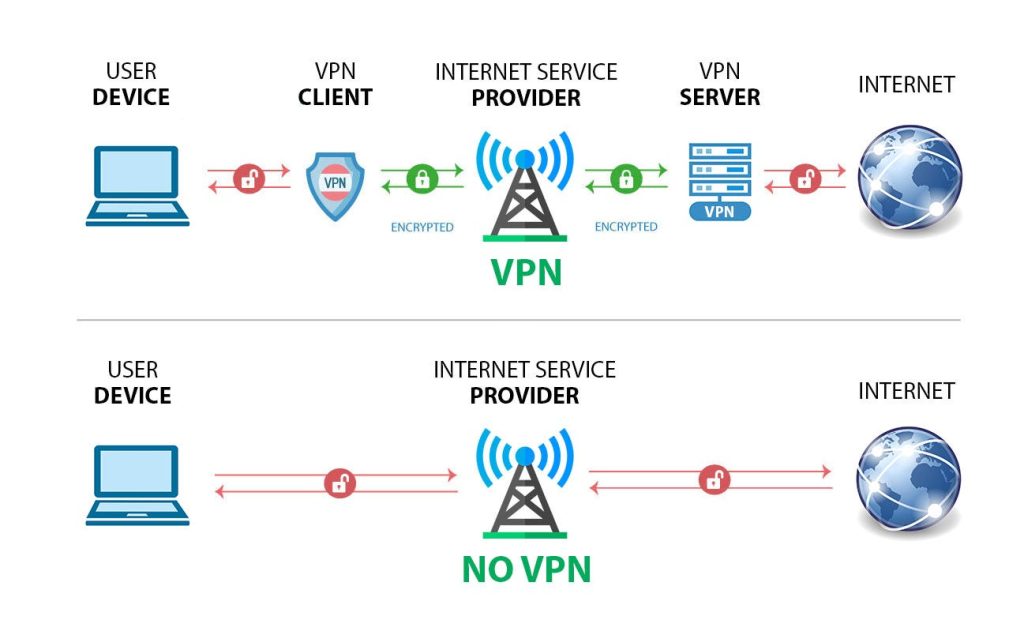
In networking, tunneling refers to the process of encapsulating one network protocol within another network protocol. This is commonly done to enable communication between networks that use different protocols or to create secure connections over untrusted networks like the internet.
Here’s how tunneling typically works:
- Encapsulation: The original data packet from one network (often referred to as the “inner packet”) is encapsulated within another packet that belongs to the protocol of the second network (often referred to as the “outer packet”). This encapsulation process effectively hides the inner packet within the outer packet.
- Transmission: The encapsulated packet is then transmitted across the network that supports the protocol of the outer packet.
- Decapsulation: Once the encapsulated packet reaches its destination, it is decapsulated to reveal the original inner packet. This process strips off the outer packet and delivers the inner packet to the appropriate destination within the receiving network.
Tunneling can be used for various purposes in networking, including:
- Virtual Private Networks (VPNs): Tunneling is a fundamental component of VPNs, where it’s used to create secure, encrypted connections over public networks like the internet. Protocols like IPsec, OpenVPN, and L2TP use tunneling to establish VPN connections between remote users and corporate networks.
- IPv6 Transition: Tunneling is used during the transition from IPv4 to IPv6 to enable communication between networks running different versions of the IP protocol. Protocols like 6to4, Teredo, and ISATAP encapsulate IPv6 packets within IPv4 packets to facilitate communication over IPv4 networks.
- Remote Access: Tunneling can enable remote access to private networks securely. For example, protocols like Secure Shell (SSH) can create encrypted tunnels for secure remote access to network resources.
- Subnet Routing: Tunneling can be used to route traffic between geographically separated parts of the same network. For instance, organizations might use tunneling to connect separate branch offices.
Overall, tunneling plays a crucial role in enabling communication and secure connections across heterogeneous networks in modern networking environments.
What is difference from VPN and Tunnel?
A VPN (Virtual Private Network) and a tunnel are related concepts in networking, but they serve different purposes and operate at different levels.
VPN (Virtual Private Network):
- A VPN is a technology that allows users to create a secure, encrypted connection over a public network (usually the internet) to a private network.
- VPNs provide users with secure access to resources on a private network, even when they are physically located outside of that network.
- VPNs can be used for various purposes, including remote access to corporate networks, bypassing geo-restrictions on content, and enhancing online privacy and security.
- VPNs typically involve the use of encryption and authentication mechanisms to ensure the confidentiality and integrity of data transmitted over the VPN connection.
- VPNs can utilize tunneling protocols (such as IPsec, OpenVPN, or L2TP) to establish secure connections between the user’s device and the VPN server, effectively creating a “tunnel” through which data can securely travel.
Tunnel:
- A tunnel, in the context of networking, refers to the process of encapsulating one network protocol within another network protocol.
- Tunnels are used to enable communication between networks that use different protocols or to create secure connections over untrusted networks like the internet.
- Tunnels can be established for various purposes, including IPv6 transition, remote access, subnet routing, and VPNs.
- Tunnels can be created using specific tunneling protocols (such as GRE, IPsec, or L2TP) to encapsulate and transmit data packets securely across networks.
- While VPNs often rely on tunneling to establish secure connections, not all tunnels are VPNs. Tunnels can be used for purposes other than VPNs, such as routing protocols or IPv6 transition mechanisms.
In summary, a VPN is a specific use case of tunneling technology, focused on providing secure access to a private network over a public network. Tunnels, on the other hand, are a more general concept of encapsulating one network protocol within another, which can be utilized for various purposes beyond VPNs.